Requirements
Action Required
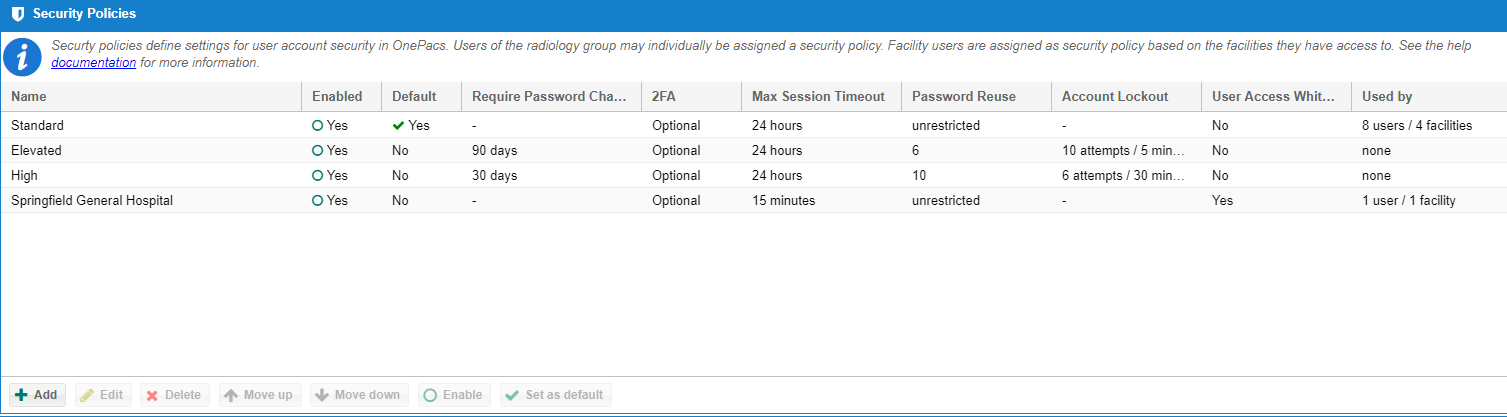
Security Policies
Overview
Security Policies in OnePacs define policies with regard to user account access settings such as passwords and session management. Security policies are configurable in OnePacs by navigating to Admin -> Security Policies.
Default Security Policy
The default security policy is the policy that is selected by default for new users of the radiology group (excluding facility users). There must be a single default security policy for your group.
To set a policy as the default security policy select an enabled security policy and click "set as default".
Ordering
Security policies are ordered in acceding order by their overall security level. That is, the least secure policies are first in the list and the most stringent policies are last in the list. Security policy ordering is only relevant for facility users that have access to more than one facility with different security policies. In that case, the most security policy will be assigned to the user on login.
To re-order a security policy, select it from the list and press "Move down" or "Move up".
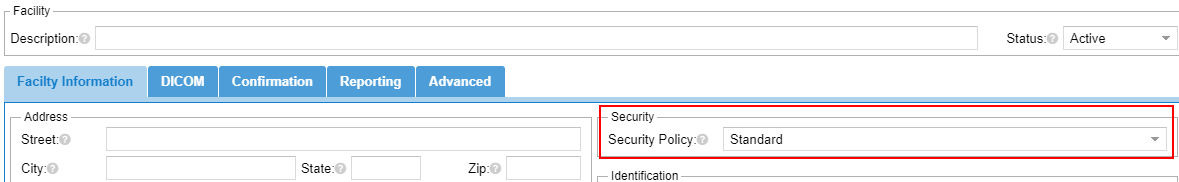
Facilities
Each facility in OnePacs designates a security policy.
The facility's security policy defines the minimal security policy for it's users that log into OnePacs.
Users
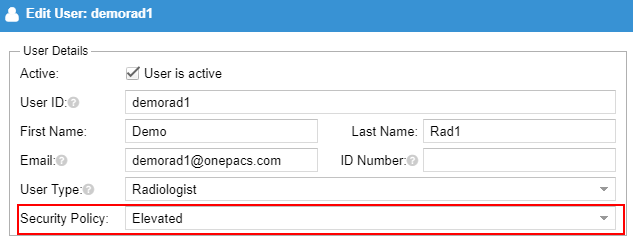
Radiology Group Users
Users of the radiology group may be assigned a security policy explicitly by an administrator when the account is created.
Facility Users
Facility users (ie users of type "Facility User" or "Facility Manager") are assigned a security policy dynamically on login. The security policy is based on the facilities the user has access to. The most stringent security policy based on the security policy ordering defined above is selected.
Security Features
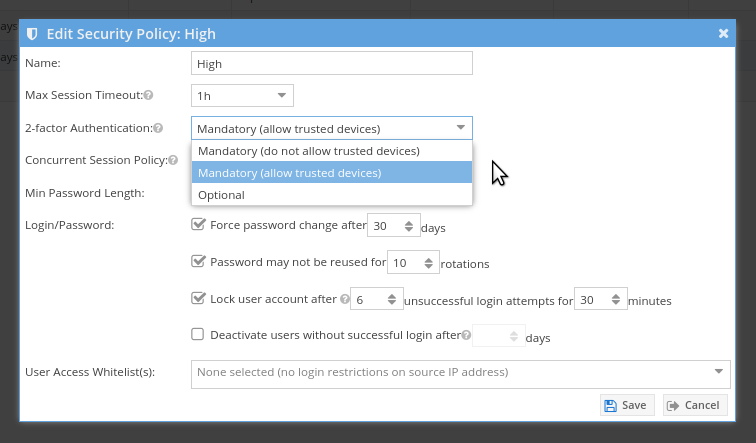
Force Password Change
The security policy may specify a mandatory password change after a configurable number of days. If enabled, users that have not changed their password within the configured number of days will be forced to change the password.
Password Reuse Policy
The security policy allows prevention of password reuse. The number of passwords that are restricted per user is configurable. If this feature is enabled, user's will not be able to reuse previous passwords up to the limit specified.
Account Lockout Policy
The security policy allows for enabling user account lockout after a configurable number of failed login attempts. Additionally, the lockout period may be configured to determine the period of time the account remains locked out. A user may clear their account lockout by resetting their password. A user manager may also clear the account lockout.
Concurrent Session Use
Use of concurrent web sessions (logins) may be restricted by user or by user/IP address. When this feature is enabled users that log in from multiple locations/computers will be prompted to forcibly log out of other sessions or cancel the current login attempt.
Maximum Session Timeout
All user sessions will time out after a configurable amount of time. This setting allows an administrator to define the maximum allowable value for session inactivity before the session is terminated.
User Access Whitelists
A security policy may define one or more user access whitelists. When a user logs in, their IP address will be compared against the whitelists defined for the security policy. If no whitelists are defined or the IP matches one or more of the configured whitelists, the user login may proceed. Users attempting login with source IP addresses that do not match the configured whitelists of the security policy will be denied login.
2-Factor Authentication
A security policy may set 2-factor authentication as either mandatory or optional.
If it is set to mandatory, users will be required to setup two factor authentication during their next login. It is also possible to indicate whether or not users are allowed to have "trusted devices" for 2FA. If users are allowed to have "trusted devices", upon successful login with 2FA the users may elect to bypass 2FA for a period of time of 7 days.
User Access Whitelists
Overview
User access whitelists define source IP addresses or IP address ranges that a user may log in from. A whitelist may have one or more IP addresses or ranges. If a user's security policy defines one or more whitelists, the user's source IP address is compared to the configured whitelists. The login request is denied if the user's IP address does not match the IP address filters defined in the user access whitelist.
IP Address Filtering
IP addresses may be filtered explicitly by an exact IP address or by an entire subnet using CIDR notation.
Examples:
4.5.6.7 <- Allow logins from 4.5.6.7
4.5.6.0/24 <- Allow logins from any IP address that starts with 4.5.6
Standard Security Features
Some security features are not configurable. They are detailed below:
Password Complexity
User password must be at least 10 characters long and contain at least one of each of the following:
- Capital letter
- Digit
- Special Character
The password may not contain the user id.
Session management / termination
User managers have the ability to view which users are logged in and view details about each session such as IP address and user agent. A user manager may forcibly terminate all user sessions.
Account Deactivation
User managers may deactivate a user account immediately or schedule deactivation for a specific date/time.
Notification of failed logins
Users are notified of failed login accounts to their configured email address. If no email address is configured an administrator is emailed. This email contains the time and the source IP address of the failed login attempt.
User login history
Successful user login and logout events are audited and retained indefinitely. Recent user login events are available to user managers by hovering of the "last login" column of the "Users" page.
Unique email address
Account registration requires a unique email address. This allows OnePacs to verify the account holder's identity when a password reset is requested.